DDoS attacks are malicious attempts to make a server or network resource unavailable to its intended users, usually by temporarily or indefinitely interrupting or suspending the services of a host connected to the internet. Unlike (DoS) “Denial of Service attack”, a (DDoS) “Distributed Denial of Service Attack” uses many computers and internet connections, in other words, more than one and often thousands of unique IP addresses.
Types DDoS Attacks
- Volume Based Attacks
The goal of volume based attacks is to saturate the bandwidth of the attacked site. These attacks include: UDP Floods, ICMP Floods, and other spoofed-packet floods.
- Protocol Attacks
This attacks consumes server resources or the resources of intermediate communication equipment, such as firewalls and load balancers.
- Application Layer Attacks
The application layer attacks are those that are comprised of seemingly legitimate and innocent requests. The purpose of this type of attack is to crash the web server. Examples of these attacks are: Slowloris, Zero-day DDoS attacks, DDoS attacks that target Apache, Windows or OpenBSD vulnerabilities.
Prevention
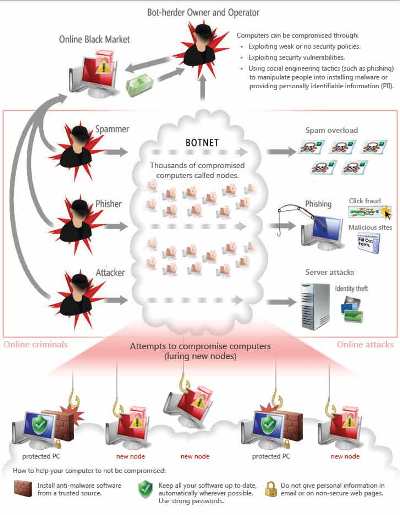
DDoS attacks are performed by networks of computers known as botnets. Botnets are created when malicious users distribute malware that can turn your computer into a bot (enlist your computer to form part of their botnet without your consent.) This will cause your compute to perform automated tasks over the internet without your knowledge.
- Install antivirus and antispyware programs from a trusted source. Anti-malware programs scan and monitor your computer for known viruses and spyware. When they find something, they warn you and help you take action.
- Keep all software up to date. Regularly install updates for all your software and subscribe to automatic updates wherever possible.
- Use strong passwords and keep them secret. You can use the contro panels password to determine the strength of your passwords.
- Never turn off your firewall. A firewall puts a protective barrier between your computer and the Internet. Turning it off for even a minute increases the risk that your PC will be infected with malware.
Do not be tricked into downloading malware!
Attackers can enlist your computer in a botnet by:
- Delivering malware in downloads that you think are pictures or movies, or through links that you click in an email or instant messages (IM), or on a social network.
- Scaring you into clicking a button or link they supply with fake warnings that your computer has a virus.




